There are two logically separate steps when provisioning a vFN chain as a set of containers: scheduling (placement and invocation of containers that represent the vNFs in the chain) and plumbing (providing network connectivity and packet flow control through the vNF chain)
Container Scheduling
Container scheduling is the concept of deciding on which compute node a container should be invoked. This needs to take into various constraints such as:
- affinity to other vNFs
- security
- compute loads
- compute stability
- ...
Container management solution typically have a logic that determines scheduling of containers. Part of the responsibility of this brigade will be able to understand what can be accomplished using the existing scheduling algorithms of the container management systems. It is possible that different behaviors may be available when executing under different container management systems (i.e. Kubernetes v. Docker Swarm Mode) and the goal is not to make the systems perform identically. Thus, part of the selection of a container management system for a given deployment may include which capabilities fit a a site's needs more appropriately.
While is it acceptable to provide plugins to augment scheduling logic if a container management system allows such plugins, it is not acceptable to have a custom fork of a container management system. The use of containers should only use the public interfaces for the container management system and as much as possible strive to use declarative configuration over plugins or code augmentation.
Network Plumbing
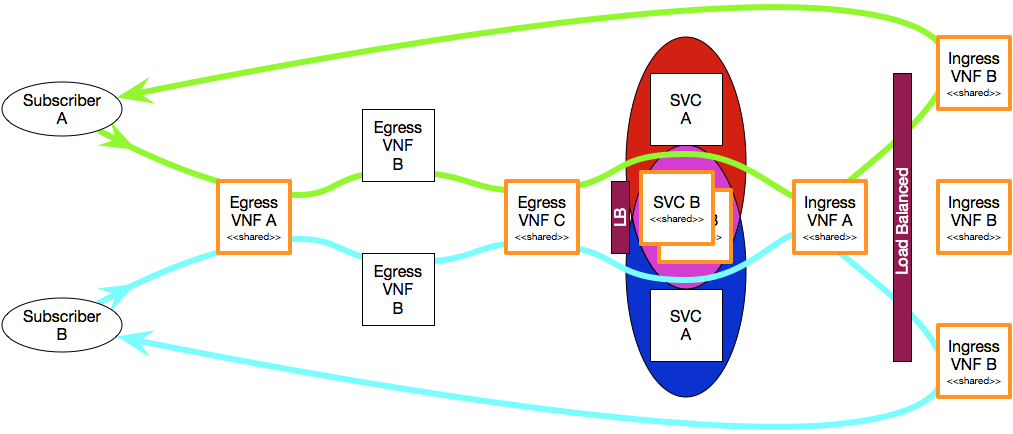
There are two aspects of network plumbing that need to be considered, chaining and network virtualization. The first (chaining) refers to flowing a packet down a specific chain of vNFs via L2 and the second (network virtualization) refers to providing a network space for a tenant that utilizes L3 routing. It should be noted that these two concepts an be interwoven such that packets flow out of a chain into a virtual network and then back through another chain, perhaps to another virtual network. The image below conceptually demonstrates these two concepts.